Identity Federation: who cares?
Today I twitted something like:
Mauro vs. ADFS + trusted custom identity provider: 1 - 0 :-) tomorrow will be harder :-)
And my dear friend Igor replied something like:
I’m really curious to know the usage scenario of ADFS
What does “Identity” mean?
Identity is a really simple concept that we face day by day in our life, each time we meet a friend we immediately recognize him, or her, given a set of well known criteria: face, voice, behavior, etc.…
We own the set of criteria that let us recognize our friends, but what happens when we meet someone we have never met before and that claims to be a specific person?
Identity Providers
We obviously need to rely on someone we trust, we can ask to the unknown party the identity card (with a photo ID, a first name and a last name) and since we trust the issuer od the identity card we can trust the person that claims to a specific person.
So far and so good…but…
What happens when we are in a foreign country and someone asks us about our identity? we can provide our own passport (with photo ID, first name, last name and issuer country)…but why the relying party should trust our passport? basically because she trusts her own government that itself trusts our government that is the issuer of the identity.
The relying party government and our government are federated by a trust relationship, this is identity federation :-)
So what?
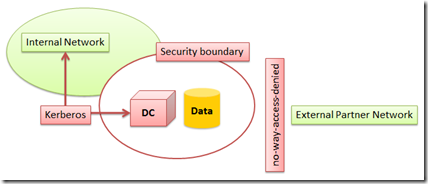
Don’t you see the big picture? Let’s say that we work for an international shipment provider, the company delegates a lot of the work to partners outside of the company domain, but these partners need to have access to information secured behind the company domain based security infrastructure:
But there is no way to have an account for the partner created in the company domain, can we “steal” some concepts from the above passport sample?
- One employee of one of the partners tries to access internal data;
- The internal security system asks the employee for credentials;
- obviously the partner employee credentials cannot be validated by the company domain controller;
- the partner employee go to its own security system, authenticates and asks for a security token (the passport);
- goes back to the company domain controller and presents the security token (the passport);
- since the company domain controller trusts the partner security system the company domain controller:
- goes back to the partner security system and verifies the validity of the issued token;
- asks to the partner security system a set of information (first name, last name, photo in other words “claims”) required by the company to allow the access;
We obtained that the security credentials of the partner employee are stored in one single place and are managed by the organization that owns those credentials.
But…Active Directory does not provide all these features, so who is the orchestrator that can link together different security systems? (as you may have notice I’ve never said that the partner security system is Active Directory, too easy :-P)
Please welcome the A.ccess C.ontrol S.erver
The ACS in our scenario is something that can manage trust relationships between different security systems, is something that can translate the language spoken by Active Directory and the language spoken by the Asp.Net MembershipProvider into something common, that is based on a shared concept: claims.
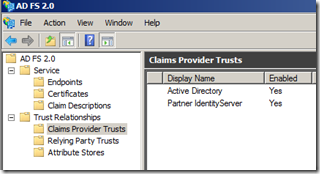
So what happens is that our shipment company installs Active Directory Federation Services (ADFS) and configure two different trusted claims provider:
- The “Active Directory” claims provider is the company internal Active Directory;
- The “Partner IdentityServer” is the external trusted IdentityProvider (in this case a custom Security Token Service and Identity Provider based on Asp.Net Membership);
The last step
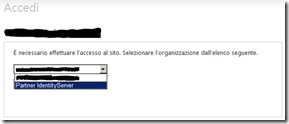
When an anonymous user tries to access the company internal application he is presented with the authentication procedure:
Where the use need to select the identity provider to use to start the authentication process.
We miss two steps:
- the client application configuration;
- the ability to automatically determine the identity provider without exposing to anonymous users the list of the supported providers;
but those are for another story :-P
.m